Client-Side Proxy vs Server-Side Proxy
Understanding forward proxies and reverse proxies from first principles, plus how they differ from VPNs and firewalls
Appreciate you reading this newsletter, I am writing as I learn and explore these topics in depth. I hope the content and resources are helping you level up as an engineer. If you want me to write about something specific, just message me or comment on the post.
Note: This article on was originally published on my personal website - https://pradyumnachippigiri.dev/blogs/forward-proxy-vs-reverse-proxy
Here’s what I learned this week
Let’s start with a very simple analogy to understand the both proxy types, and then let’s understand what they are, why they are used.
Simple Analogy for Client-Side Proxy
Imagine you are a very famous person, and you want to buy vegetables for cooking, but you don’t want anyone to recognize you. So you send your personal assistant to the store to buy them for you. The store owner only sees the assistant, sells the vegetables, and has no idea who they’re actually for. In other words, your assistant is hiding your identity from the outside world.
Here:
You are the client
Your personal assistant is the forward proxy
The store / store owner is the internet website / server
So a forward proxy sits between the client and the internet, makes requests on behalf of the client, and helps hide the client’s identity (plus it can apply rules like allow/block/log if needed).
Simple Analogy for Server-Side Proxy
When you go to a restaurant and want to order food, you don’t walk into the kitchen and talk to the chefs directly, right? Instead, you place your order with the waiter/host. They check the menu, make sure the order is valid, and then pass it to the chef so it can be prepared.
In this scenario:
You are the client
The waiter/host is the reverse proxy (server-side proxy)
The chef/kitchen is the server.
So the reverse proxy’s job is to sit in between and make sure the client doesn’t interact with the server directly, it accepts the request, applies rules/filters if needed, and forwards it to the right server. The reverse proxy(the host/waiter) is protecting and managing the kitchen (server) from bad/too many/invalid requests.
Hope you got a fair understanding with this analogy, but now let’s dive in.
What is Proxy ?
Proxy is nothing but a machine that sits between 2 systems. A proxy terminates the incoming connection and initiates a new, separate connection to the destination.
It acts like an intermediate layer that can:
apply rules (allow/block),
route traffic,
hide details of the other side,
and make communication more controlled and predictable.
Common misconception is that it can be only between a client and a backend servers, but it can also be between 2 backend servers too.
Depending upon the kind of proxy that we are using in our system, it will have different applications:
Forward Proxy: This type of proxy is used to protect the clients accessing the websites via the internet.
Reverse Proxy: This type of proxy is used to guard the web servers from the clients trying to access websites via the internet.
Let’s understand about each of them in depth.
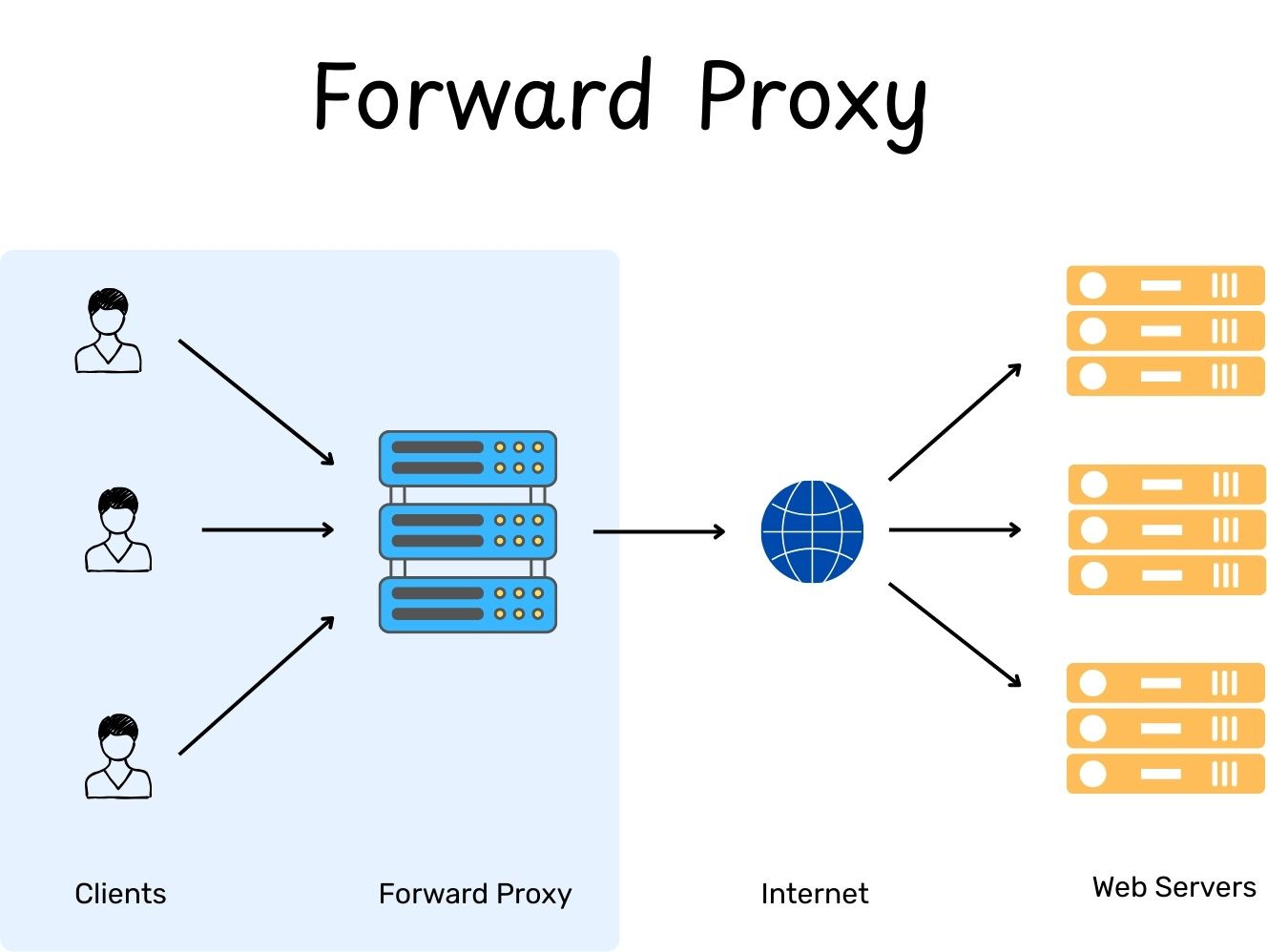
Forward Proxy (Client-Side Proxy)
Forward Proxy (also called a client-side proxy or internet-facing proxy) sits between the client and the internet (for example, between your browser and a website). So whenever your browser makes a request, it sends (in plain text without encryption) that request to the forward proxy first. The forward proxy can decide whether to allow it, block it, or route it to the correct destination server.
Then the destination server sends the response back to the forward proxy, and the forward proxy forwards that response back to your browser.
So the forward proxy’s job is to act as a middleman for the client, it can hide the client’s real identity (IP) from the internet and also control/log what the client is allowed to access.
Advantages of Forward Proxy
Content filtering and security : They can filter out unwanted or dangerous content. Proxies can block access to specific sites and protect the network by filtering out suspicious requests or malicious files before they reach the user.
Anonymity: A forward proxy hides the client’s IP address from the destination server. Since the server only sees the proxy’s IP, it makes it much harder to track individual user activity or target specific clients for an attack.
Caching : Forward proxies cache frequently requested resources. When another requests the same data, the proxy serves it directly from its cache instead of fetching it from the internet. This reduces bandwidth usage and speeds up load times.
Request Modification: Proxies can modify outgoing requests by adding or removing headers. (can also group multiple requests as one) This allows an organization to customize how traffic looks to the outside world or strip away sensitive information for better privacy.
Access Control: They enforce strict rules on who can access the internet. By requiring authentication and authorization, the proxy ensures that only permitted users or devices can reach external resources.
Real world example : I’ve seen this in my universities and corporate office. All internet traffic is routed through a proxy, so every request I make has to pass through that single checkpoint. If I try to access something that’s blocked, say a restricted website, the proxy immediately detects it and cuts the connection based on predefined rules. This is how organizations, control what content is allowed within their networks.
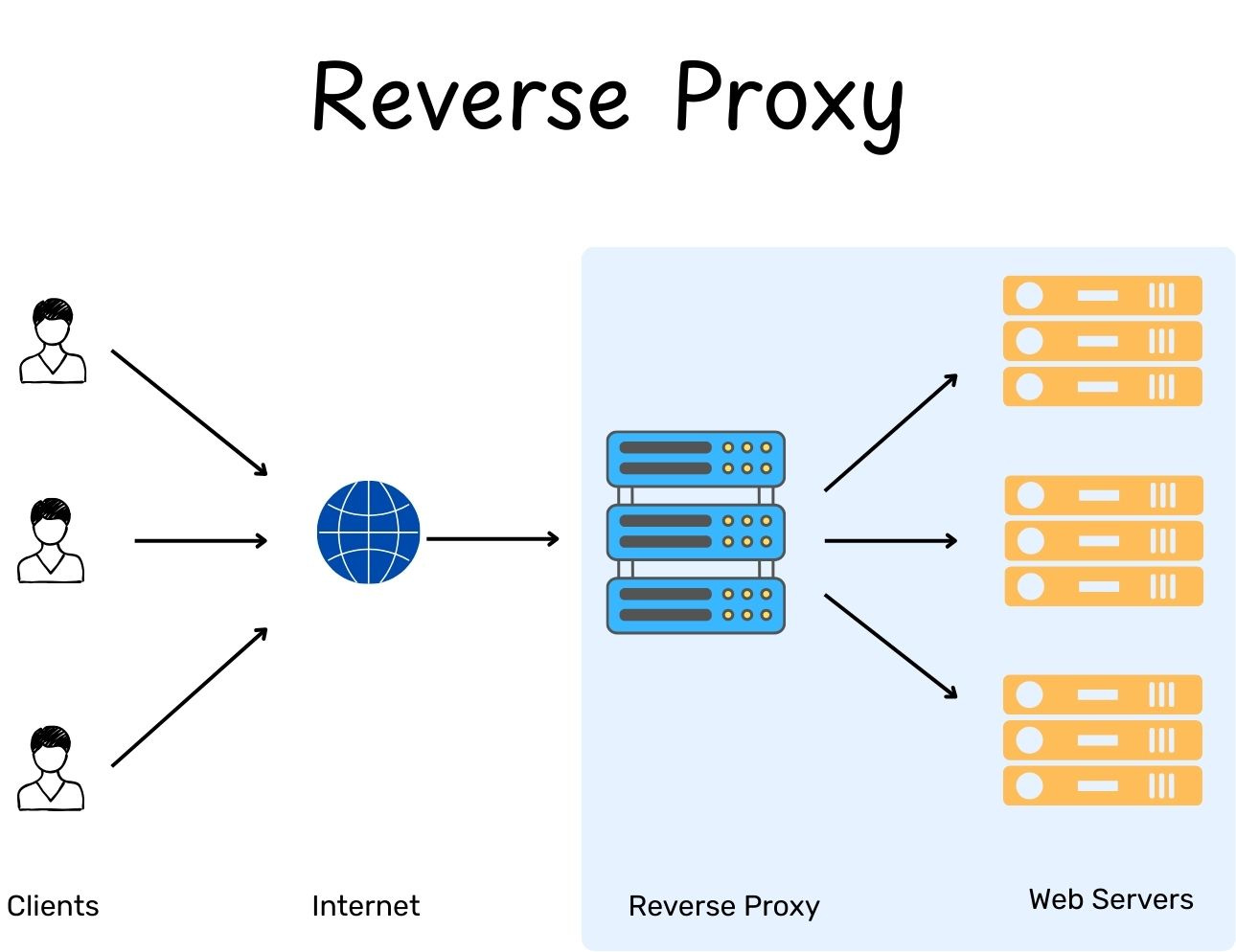
Reverse Proxy (Server-Side Proxy)
A Reverse Proxy (Server-Side Proxy / internal-facing proxy) sits between the internet and the web servers (the destination). When a user makes a request to a website, the request hits the Reverse Proxy first. The proxy then decides which backend server should handle the request. Once the server finishes the job, it sends the data back to the proxy, which then passes it back to the user.
While a forward proxy acts as a middleman for the client, a reverse proxy acts as a middleman for the server. It hides the servers’ real identity and protects them from the internet. It abstracts away the complexity of the downstream systems.
Advantages of Reverse Proxy
Load Balancing: Reverse proxies act as traffic controllers. They distribute incoming requests across multiple servers so that no single server gets overwhelmed.
Server Protection & Security: The proxy acts as a shield. It hides the real IP addresses of the backend servers, making it impossible for hackers to target them directly. It can also block DDoS attacks or suspicious traffic before it even reaches the actual data.
SSL Termination: Handling the HTTPS lock icon (encryption) is heavy work for a server. The reverse proxy handles all the encryption and decryption, freeing up the backend servers to focus strictly on its tasks.
Caching: Reverse proxies can cache frequently requested resources, reducing the need for repeated requests to the web servers.
Response Modification & Compression: The proxy can shrink files (compression) to make them load faster on your phone. It can also add or remove information from the server’s response (headers) to make it more secure before it reaches the user.
Example :
An API Gateway is a specialized reverse proxy built for APIs
A load balancer (as it splits traffic across servers, it abstracts out the number of servers are there what they do) is a specialized reverse proxy for traffic distribution.
Db Proxies are specialized form of reverse proxy (sits infront of databases. It abstracts the database layer, handles connection pooling, and caches common query results.)
CDN (Content Delivery Network): A specialized, globally distributed reverse proxy. While a normal proxy sits in one data center, a CDN places edge proxies in hundreds of cities worldwide. It caches static content (like images and videos) as close to the user as possible to reduce latency.
Reverse Proxy can be all of these, but all of these cant be a reverse proxy.
Industry-Standard Reverse Proxies: Nginx, HAProxy, Kong Gateway, ProxySQL,
Some must know differences when it comes to this topic would be:
Proxy vs VPN
VPN : A VPN creates a secure, encrypted tunnel for all the device's traffic (browsers, apps, system updates). It is secure because it encrypts your data, unlike proxies where it sends in plain text (unencrypted). (hides IP system-wide)
Proxy : It only works at the application level (e.g., just your web browser). It doesn't usually encrypt your data; it just masks your IP address for that specific app. It allows only for one app not system wide. (hides IP app-level)
Proxy vs Firewall
Firewall : firewall sits at the edge of the network and scans incoming and outgoing data packets (it only looks at the header of the data (IP and Port). It does not open the data. It can block/allow connections instantly based on rules, no need to terminate the connection), If the data is coming from a suspicious source, the firewall stops it at the door before it can get into your computer. So it just filters and blocks, it does not have proxy characteristics like caching.
Proxy : It is a middleman that terminates the client connection and starts a new connection to the server. Because it acts as the destination, it can "read" the data to perform caching or content filtering.
Hope you liked this article. If you did, please give it a like. If you have any questions or thoughts, drop a comment, this could spark a great discussion.
The next two articles are going to be about MVCC and my favorite Bloom Filters so stay tuned.
And if you enjoy this kind of content, do follow me on LinkedIn and X for more.
And if you’d like to support my work, you can also buy me a coffee by clicking the link below, it really helps and means a lot.




Solid breakdown of proxies, especially the waiter analogy for reverse proxies. The way that maps to actul production systems (like CDNs being distributed reverse proxies) really clarified something I've dealt with but never fully thought through. In my experience working with API gateways, I noticed how they handle rate limting before requests hit backend services, but seeing that as fundamentaly a 'shielding' mechanism makes it click way better.